Computer hacking is most common among teenagers and young adults, although there are many older hackers as well. Many hackers are true technology buffs who enjoy learning more about how computers work and consider computer hacking an “art” form. They often
enjoy programming and have expert-level skills in one particular program. For these individuals,computer hacking is a real life application of their problem-solving skills. It’s a chance to demonstrate their abilities, not an opportunity to harm others.
Since a large number of hackers are self-taught prodigies, some corporations actually employ
computer hackers as part of their technical support staff. These individuals use their skills to find flaws in the company’s security system so that they can be repaired quickly. In many cases, this type of computer hacking helps prevent identity theft and other serious computer-related crimes. Common Methods for Hacking.
Computer Servers:
This comprises of either taking control over terminal(or Server) or
render it useless or to crash it..
following methods are used from a
long time and are still used..
Phishing
 This is another type of keylogging,
This is another type of keylogging,here you have to bring the user to a
webpage created by you resembling
the legitimate one and get him to
enter his password, to get the same
in your mail box..!! Use social
engginering..
 Distributed DoSs
Distributed DoSs
Distributed DoSs (DDoSs) are
coordinated DoS attacks from
multiple sources. A DDoS is more
difficult to block because it uses
multiple, changing, source IP
addresses.
 Denial of Service
Denial of Service
DoS attacks give hackers a way to
bring down a network without
gaining internal access. DoS attacks
work by flooding the access routers
with bogus traffic(which can be e-
mail or Transmission Control Protocol, TCP, packets).
Sniffing
Sniffing refers to the act of intercepting TCP packets. This interception can happen through simple eavesdropping or something more sinister.
Spoofing
Spoofing is the act of sending an illegitimate packet with an expected acknowledgment (ACK), which a hacker can guess, predict, or obtain by snooping.
SQL injection
SQL injection is a code injection
technique that exploits a security
vulnerability occurring in the
database layer of an application. It
uses normal SQL commands to get
into database with elivated
privellages..
Viruses and Worms
Viruses and worms are self-
replicating programs or code
fragments that attach themselves to
other programs (viruses) or
machines (worms). Both viruses and
worms attempt to shut down
networks by flooding them with
massive amounts of bogus traffic,
usually through e-mail.
Back Doors
Hackers can gain access to a network by exploiting back doors administrative shortcuts, configuration errors, easily deciphered passwords, and unsecured dial-ups. With the aid computerized searchers (bots), hackers can probably find any weakness in the network. So, not interested in these stuffs.. huh??? wait there is more for you.. So, how about the one related to hacking the passwords of email and doing some more exciting stuffs..
The various methods employed for
this are:
Trojan Horses
Trojan horses, which are attached
to other programs, are the leading
cause of all break-ins. When a user
downloads and activates a Trojan
horse, the software can take the full
control over the system and you can
remotely control the whole system..
great..!!! They are also reffered as
RATs(Remote Administration tools)
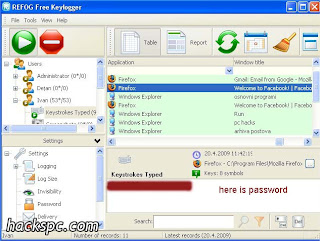
Key loggers
Consider the situation, everything
you type in the system is mailed to
the hacker..!! Wouldn't it be easy to
track your password from that..
Keyloggers perform similar
functionallities.. So next time you
type anything.. Beware..!! Have
already posted about keyloggers and
ways to protect yourself from
them..
Brute Forcing
The longest and most tiring job.. don't even consider this if you don't
know the SET of password for your victim..
Secret Question
According to a survey done by security companies, it is found that rather than helping the legitimate users the security questions are more useful to the hackers.. So if
you know the victim well try this..
Social Engineering
Ya this was one of the oldest trick to
hack.. Try to convince your user
that you are a legitimate person
from the system and needs your
password for the continuation of
the service or some maintainence..
This won't work now since most of the users are now aware about the Scam.. But this Social Engginering concept is must for you to have to convince victim for many reasons..!
Fake Messengers
So its a form of phishing in the application format.. getting user, to enter the login info in the software and check your mail..!!!
Cookie Stealer
Here the cookie saved by the sites are taken and decoded and if you get lucky.. You have the
password..!!! Hmmm.. not satisfied with single account at a time..?? so there are ways to hack lots of accounts together.. I know few but there exists many..!! listed are the ones i
know and will teach you in coming posts...
DNS Poisoning or PHARMING
So, phishing is a tough job.. isn't
it..?? convincing someone to enter
their password at your page..??
what if you don't have to
convince..?? what if they are
directed automatically to your site
without having a clue..?? Nice huh..?? Pharming does the same for you.. More about it in my next post..
Whaling
This method gets you the password of the accounts which are used by the hackers to recive the
passwords.. So you just have to hack one ID, which is simplest method( Easy then hacking any
other account, will tell you how in coming posts..) and you will haveloads of passwords and so loads of accounts at your mercy..!!!













0 comments :
Post a Comment